This week, compromised email accounts expose IT infrastructure, ransomware leads to company data misuse, and cybersecurity incidents are expected to rise this Holiday season.
Dark Web ID Trends:
Top Source Hits: ID Theft Forums
Top Compromise Type: Domain
Top Industry: Education & Research
Top Employee Count: 101 – 250 Employees
United States – Select Health Network
Exploit: Unauthorized email account access
Select Health Network: Indiana-based collection of healthcare providers
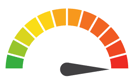 | Risk to Small Business: 1.444 = Extreme: An employee’s compromised email account credentials were used to access sensitive data for thousands of patients. The data was accessed between May 22 and June 13, and it’s unclear why it took the company so long to identify the breach and to report it to patients. Regardless, a small vulnerability will likely result in a sizeable blowback in the form of regulatory scrutiny, brand erosion, and potential financial repercussions. |
 | Individual Risk: 2.142 = Severe: Hackers had access to patient data, including names, addresses, dates of birth, member identification numbers, treatment information, health insurance details, medical history information, and medical record numbers. In addition, some patients’ Social Security numbers were accessible. Those impacted by the breach should know that their credentials could have already been misused, and they should take steps to evaluate their data integrity while also ensuring long-term security. |
Customers Impacted: 3,582
How it Could Affect Your Customers’ Business: Small security lapses can have serious consequences, as evidenced by the expansive breach resulting from one compromised employee account. However, companies have an obligation to support their customers after a breach and identifying what happened to their data after it was stolen is a good place to start. Taking the right course of action to support customers after a breach can go a long way towards repairing the reputational damage that can have far-reaching repercussions.
United States – PayMyTab
Exploit: Accidental data exposure
PayMyTab: Hospitality payment platform
 | Risk to Small Business: 2 = Severe: Cybersecurity researchers located an unsecured Amazon Web Services bucket that contained the personal data for tens of thousands of PayMyTab users. Notably, the data packet was exposed because PayMyTab personnel failed to follow Amazon’s security protocols. Fortunately, the error was discovered by white hat hackers and was reported to the company, but the bucket had been exposed since July 2, 2018, giving bad actors plenty of time to locate and exploit the information first. |
 | Individual Risk: 1.428 = Severe: User data was openly exposed to the internet, including customer names, email addresses, telephone numbers, order details, restaurant visit information, and the last four digits of payment card numbers. Those compromised by the breach should know that this information can be repurposed by cybercriminals to perpetuate other cybercrimes like phishing attacks. In addition, consider alerting your card issuer to the breach and ensure that your payment card information isn’t misused. |
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Understandably, SMBs sometimes fall short in funding cybersecurity initiatives, but compromises can stifle growth and innovation. This incident was an entirely avoidable mistake, and it’s one that could cost the company as it seeks to expand its customer base and capabilities. More than that, it’s a reminder that a great idea can be stymied by failing to account for the vulnerabilities that accompany improvements in user experience.
ID Agent to the Rescue: It’s critical that your SMB customers understand the importance of cybersecurity. Goal Assist™ is an expansion of our White Glove Support that includes hands-on assistance with your direct sales interactions. Let us help to ensure you are getting the most from your Partnership selling Dark Web ID. ID Agent’s Partner Success Team will set you up for the win! Learn more here: https://www.idagent.com/goal-assist.
United States – Solara Medical Supplies
https://www.beckershospitalreview.com/cybersecurity/medical-supplies-company-alerts-patients-employees-of-data-breach.html
Exploit: Compromised email account
Solara Medical Supplies: Supplier of diabetes-related treatment products
 | Risk to Small Business: 1.444 = Extreme: An unauthorized third-party gained access to several employee accounts containing patient and employee data. The breach was first discovered on June 20th, and the compromised data was exposed between April 2nd and June 20th. In response, the company reset account passwords, and Solara is updating its policies to ensure that a similar scenario doesn’t occur again in the future. Unfortunately, such maneuvers won’t help patients whose data was already stolen in the breach. Moreover, the company’s lengthy response time will certainly invite increased regulatory scrutiny while giving consumers fodder for criticism during the recovery effort. |
 | Individual Risk: 2.142 = Severe: Personal information, including names, addresses, dates of birth, Social Security numbers, employee identification numbers, medical information, health insurance information, financial information, credit/debit card numbers, password information, Medicare/Medicaid numbers, and billing information were all at risk. This comprehensive data set can quickly be distributed on the Dark Web, where it can be used to execute even more egregious cybercrimes. Those impacted by the breach should take every precaution to ensure that their data isn’t being misused. |
Customers Impacted: 82,577
How it Could Affect Your Customers’ Business: Preventing a data breach begins with accounting for your vulnerabilities. One of the easiest yet most important cybersecurity initiatives that businesses should undertake is tightening up security around company email accounts. Whether your business fortifies credentials with strong, unique passwords and two-factor authentication or it integrates active monitoring protocols to evaluate data movement, password protection is quickly becoming a “can’t miss” component of any data security strategy.
United States – Allied Universal
Exploit: Ransomware
Allied Universal: Facility services retailer
 | Risk to Small Business: 2.111 = Severe: Cybercriminals encrypted the company’s IT infrastructure with Maze Ransomware, leaving behind a ransom demand that exceeded $2 million. When the company failed to pay by the instituted deadline, the hackers escalated the attack, publishing 700MB of company data online. Not only will this significantly complicate recovery efforts, the company will be responsible for sending data breach notifications to any impacted individuals. Notably, hackers have threatened to use Allied Universal’s domain name and email accounts to initiate spam campaigns. |
 | Individual Risk: 2.428 = Severe: While ransomware often spares individual’s personal data, there is no honor among thieves, and users’ personal data could be compromised by this attack. Customers should be on the lookout for evidence of data misuse, and, given the hackers’ threat, they should be especially critical of messages purportedly originating from the company. |
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: This is an incredibly expansive data breach for an SMB, and the repercussions are bound to be both expensive and far-reaching. Even when companies decline to submit to demands, the recovery costs can easily exceed the ransom payment. Coupled with additional data exposure, the price tag on such an incident could be immense. Ransomware is a top threat for any SMB, and the only adequate recovery is to proactively prevent malware from finding its way into your organization.
Ireland – Liver Wellness
https://www.siliconrepublic.com/enterprise/liver-wellness-medical-clinic-phishing-breach
Exploit: Phishing attack
Liver Wellness: Medical testing company
 | Risk to Small Business: 2.444 = Severe: Hackers accessed the healthcare provider’s network and sent phishing emails to their patients soliciting sensitive personal information. The first email was sent in mid-October, and Liver Wellness sent follow up emails notifying customers of the malicious messages originating from their accounts. More than a month after the first phishing email went out, Liver Wellness still hadn’t discovered how hackers accessed their accounts. This news will likely result in increased scrutiny from privacy and health regulators, while also inflicting reputational damage on the Liver Wellness brand. |
 | Individual Risk: 2.428 = Severe: Currently, officials don’t believe that any patients responded to a fraudulent email. Nevertheless, all patients of Liver Health should be especially critical of any communications from the company, especially those soliciting personal data or payment information. |
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Healthcare data breaches are becoming increasingly prevalent as hackers have identified these institutions as targets with valuable information and limited security. As a double whammy, healthcare companies already face stringent regulatory standards that can escalate the cost of failure when it comes to protecting patients’ data. In today’s digital landscape, the maxim of “first doing no harm” certainly includes protecting patients’ most sensitive personal information.
ID Agent to the Rescue: Monitoring the Dark Web for stolen credentials is critical for MSPs who want to provide comprehensive security to their customers. BullPhish ID™ compliments that data with simulated phishing attacks and security awareness training campaigns to educate employees, making them the best defense against cybercrime: https://www.idagent.com/bullphish-id.
France – Rouen University Hospital
https://www.forbes.com/sites/daveywinder/2019/11/20/infection-hits-french-hospital-like-its-2017-as-ransomware-cripples-6000-computers/
Exploit: Ransomware
Rouen University Hospital: Full-service medical facility
 | Risk to Small Business: 2.333 = Severe: A catastrophic ransomware attack encrypted the IT infrastructure for all five campuses of Rouen University Hospital. In total, more than 6,000 computers were encrypted with IT administrators, bringing the rest of the network offline to prevent malware from spreading further. Days after the attack, the hospital still hadn’t cleared the encryption. Doctors and nurses resorted to using paper medical records and making phone calls to various departments to ensure continuity of care. This incident is more than just an inconvenience, as it put lives at risk and interrupts all organizational processes. Individual Risk: No personal data was compromised in the breach, but patient care was at risk due to communication outages. |
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Once a ransomware attack takes place, most businesses struggle to execute a response plan that can recover damage to data and infrastructure. Knowing that these attacks are increasing in frequency and intensity, businesses of every size and sector need to evaluate their defensive posture and ensure that they have their bases covered.
New Zealand – Disney+
Exploit: Compromised user accounts
Disney+: Media streaming service
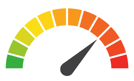 | Risk to Small Business: 1.888 = Severe: Thousands of Disney+ customers had their login credentials stolen and distributed on the Dark Web. While the data breach isn’t limited to Australian users, it coincided with the Australian launch of the streaming service, which means that the brand’s reputation was damaged before users had an opportunity to judge the service based on its merits. In a crowded marketplace, brand erosion can quickly degrade competitiveness, and these negative headlines will not help Disney’s competition against Netflix and other streaming services. |
 | Individual Risk: 2.142 = Severe: It’s unclear how hackers gained access to user accounts. Some customers admitted to reusing passwords that could have been compromised in other attacks, but some used unique passwords. It’s possible that users had credential stealing malware installed on their computers or that they responded to a phishing attack. Regardless, account details include their most sensitive personal information, and they should take every precaution to ensure that their data remains secure. At the same time, users should double check the originality of every account password, as it’s an easy way to thwart many hacking attempts. |
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Even as the cost of a data breach continues to rise exponentially, quantifiable costs aren’t the only expense that companies should consider. Brand erosion is a real problem, as customers are increasingly willing to walk away from platforms and services that can’t protect their data. No matter how you look at it, having thousands of people complaining about your service online is a terrible day for business, and could have long-term costs for the service’s viability.
Australia – Sport Australia
https://www.sportaus.gov.au/media-centre/news/a-statement-from-asc-ceo
Exploit: Compromised email account
Sport Australia: Government agency responsible for supporting and investing in athletic activities
 | Risk to Small Business: 2 = Severe: Hackers compromised an employee’s email account that caused a data security scare at the agency. After identifying suspicious activity on the account, the employee reported the abnormalities to an IT administrator who determined that the account was compromised. However, only the single employee account was impacted by the breach. While this incident appears to have spared personal data, compromised email accounts are often the gateway into an organization’s network, and they can be the catalyst for widespread data breaches that come with serious consequences. Individual Risk: Employee accounts often contained personal data, but Sport Australia isn’t reporting any compromised personal information from this breach. |
Customers Impacted: Unknown
How it Could Affect Your Customers’ Business: Securing your employees’ email accounts is one of the best ways to ensure that your network remains intact. With many login credentials already for sale on the Dark Web, businesses should implement necessary stop-gaps to ensure that their employees’ can protect company data by securing the email accounts at all times.
Risk Levels:
1 – 1.5 = Extreme Risk
1.51 – 2.49 = Severe Risk
2.5 – 3 = Moderate Risk
*The risk score is calculated using a formula that considers a wide range of factors related to the assessed breach.
